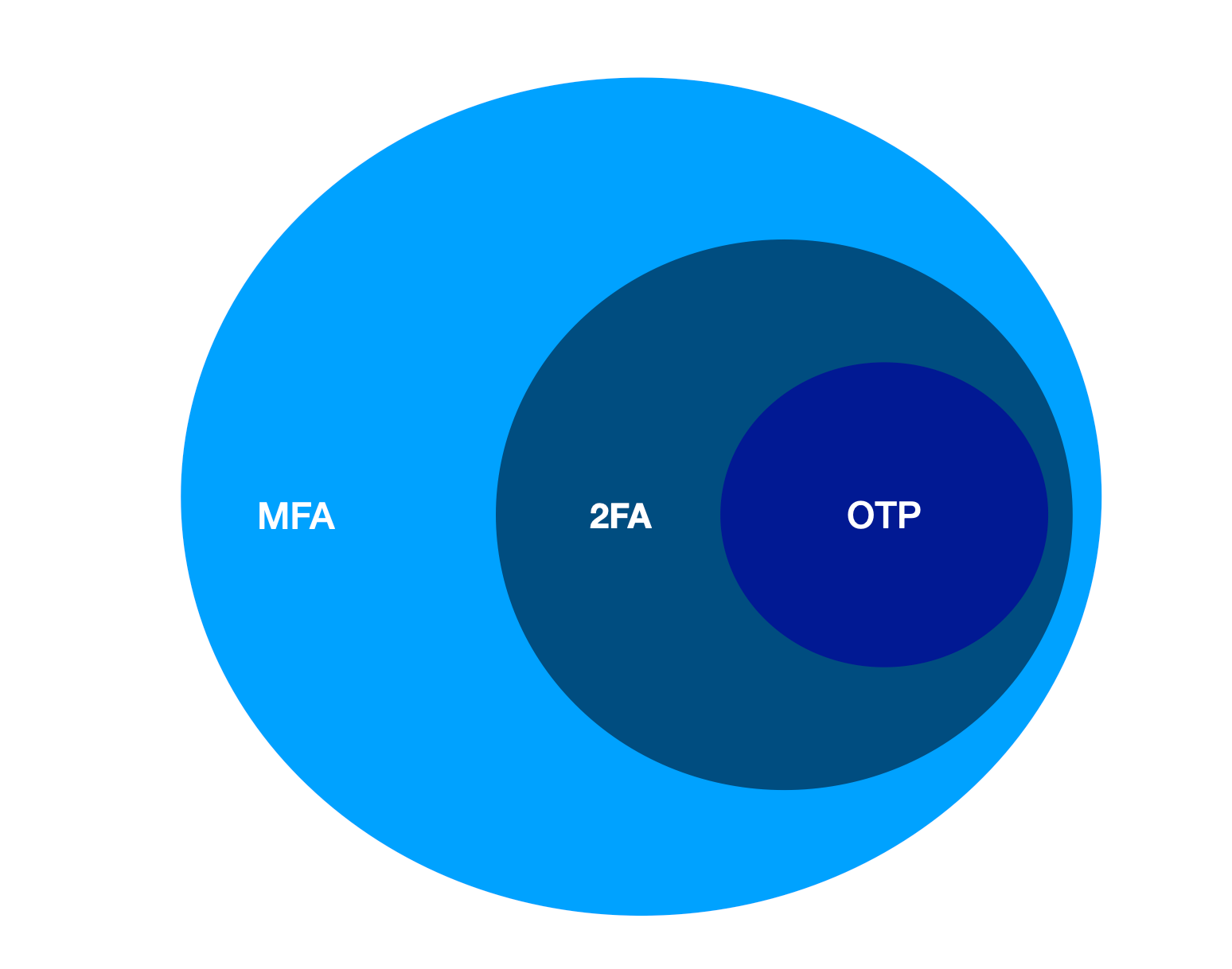
Two-Factor Authentication (2FA)
I took a good look at Two-Factor Authentication (2FA) and I explain why I prefer an authenticator app above SMS.

Our insecure digital times call for extra care and attention to your digital security. It is just like taking care of your health that good health is not a certainty, but there are some things you are better off leaving and some that it is important that you do. In matters of digital security, you need to be resilient because we are more and more depending on Cybersecurity.
For security, I prefer not to use technology that I don't fully understand myself, and so I delved into Two-Factory Authentication (2FA) and I share what I learned. Key takeaway is to prefer an authenticator app above SMS.
What is Two-Factor Authentication (2FA)?
Passwords, by themselves, are only moderate security. They are non-personally identifiable information that is also often easy to guess or find out. The name of your oldest child, cat or dog name followed by a year. Sounds familiar? We almost all do it that way because how else do you remember it all.
2FA adds an extra step to logging in. A second factor, a second something. And that would be, for example, knowledge, a possession or something from your biology. With knowledge, it could be, for example, a PIN or character string or a question that only you know the answer to. With possession, you can think of an ATM card or a cell phone. And with biology, your fingerprint or shape of the face.
With those extra factors in addition to a password, you can then use different types of 2FA. Sometimes it's hardware things, sometimes SMS, push notification, a fingerprint reader, your location, or you have to use an app that generates a number.
Two-factor authentication on an app
I was abroad the other day and wanted to log in to a 2FA secured site but unfortunately, no idea why, my SMS was no longer working. So I didn't get a number forwarded and then couldn't log in. I suddenly realized that I was now dependent on a working phone connection. That makes it pretty vulnerable.
I made a note to look into 2FA a bit further and put my experiences into an article. I had used a 2FA app in the past, but never fully understood it. This made me feel insecure because if it doesn't work then you lock yourself out. Now I have looked at it in more detail and learned something important:
The 2FA works by the server sharing a key once and with time based calculations. There is no active connection necessary for generating these numbers!
What happens is that the server where you will use 2FA sends you once a string of characters (token) that you store in an app. That app and the clock on your mobile can then be used to generate a number that matches the calculation on the server. That gives you access.
So the app is used for storing the tokens. This can then also be done for multiple accounts. Like a wallet with multiple cards. And the app then does the calculations based on time.
How to put this to work
You need to decide on which app you want to use. And with new security comes new responsibilities.
There is a risk of losing the tokens. So some providers give you a series of backup codes that you then have to store somewhere. Quite a messy arrangement if you do a lot with 2FA. Another approach is to have secure cloud storage for your tokens.
By looking at 2FA more closely, I discovered that Apple now offers a build in 2FA that is also stored in the cloud. Having this build into the browser gives convenience. But the popular app Authy for Twilio can do the same, you need to be on Chrome and then there are plugins.
Bottom line, whatever app you choose for storing the tokens and generating the one time passwords, it is more resilient and safe than using SMS. It is also more private because you don't have to sprinkle your mobile phone number around. And I truly hope that with this explanation you got a better understanding, and you feel more confident in using the technology.



